A) Schematic showing key parameters of breach width (Bw) and
4.5 (95) · $ 11.50 · In stock
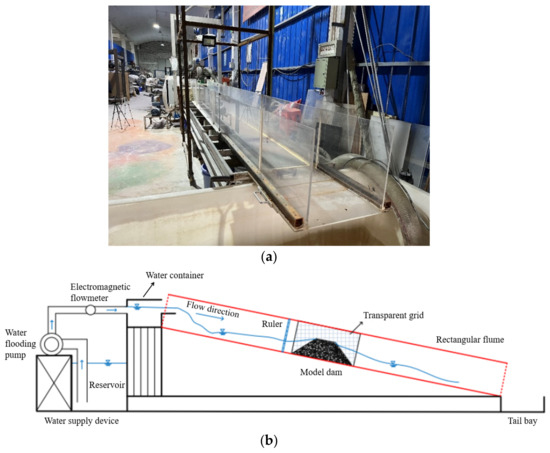
Materials, Free Full-Text

PDF) Glacial lake outburst flood hazard under current and future conditions: first insights from a transboundary Himalayan basin

Owen KING, PhD Student, BSc Geography-Geology, MSc Glaciology, University of Leeds, Leeds, School of Geography

Ashim SATTAR, Assistant Professor IIT Bhubaneswar; Former Faculty (DST Inspire) @ IISc Bangalore; Former Postdoc @ University of Zurich and Uni. of Dayton, Ohio, USA; Scientific consultant UZH- Mountain Hazards

Schematic diagram of a breach cross section, where hw is the

Data security crisis in universities: identification of key
NHESS - Invited perspectives: Managed realignment as a solution to
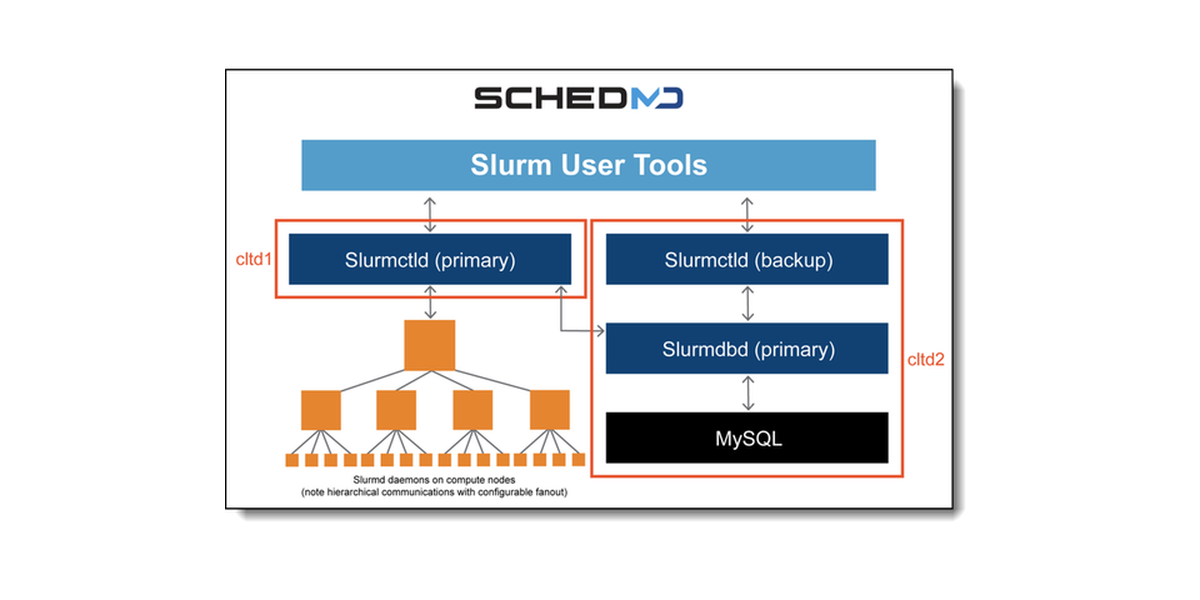
Lenovo Compute Orchestration in HPC Data Centers with Slurm

Breaching Active Directory tryhackme, by abdellah oullaij

Ashim SATTAR, Assistant Professor IIT Bhubaneswar; Former Faculty (DST Inspire) @ IISc Bangalore; Former Postdoc @ University of Zurich and Uni. of Dayton, Ohio, USA; Scientific consultant UZH- Mountain Hazards

Ashim SATTAR, Assistant Professor IIT Bhubaneswar; Former Faculty (DST Inspire) @ IISc Bangalore; Former Postdoc @ University of Zurich and Uni. of Dayton, Ohio, USA; Scientific consultant UZH- Mountain Hazards

Tobias BOLCH, Reader (Associate Professor), PD Dr., University of St Andrews, Saint Andrews, School of Geography and Sustainable Development
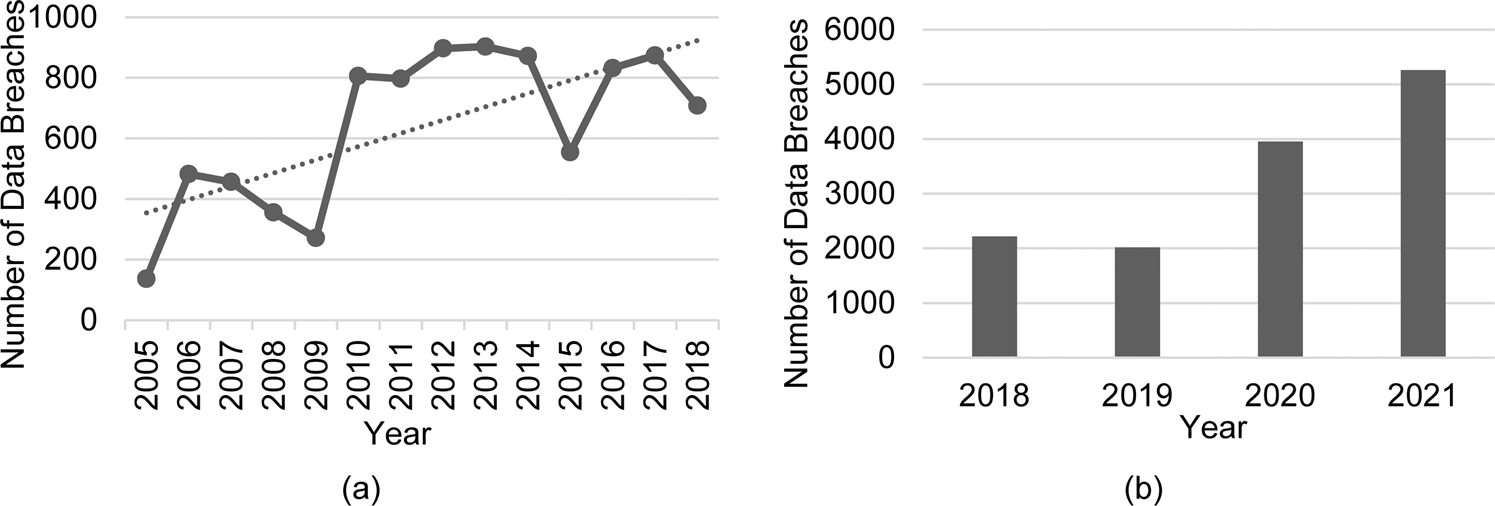
Data security crisis in universities: identification of key

Schematic diagram with geometric parameters of a typical dam










,aspect=fit)
