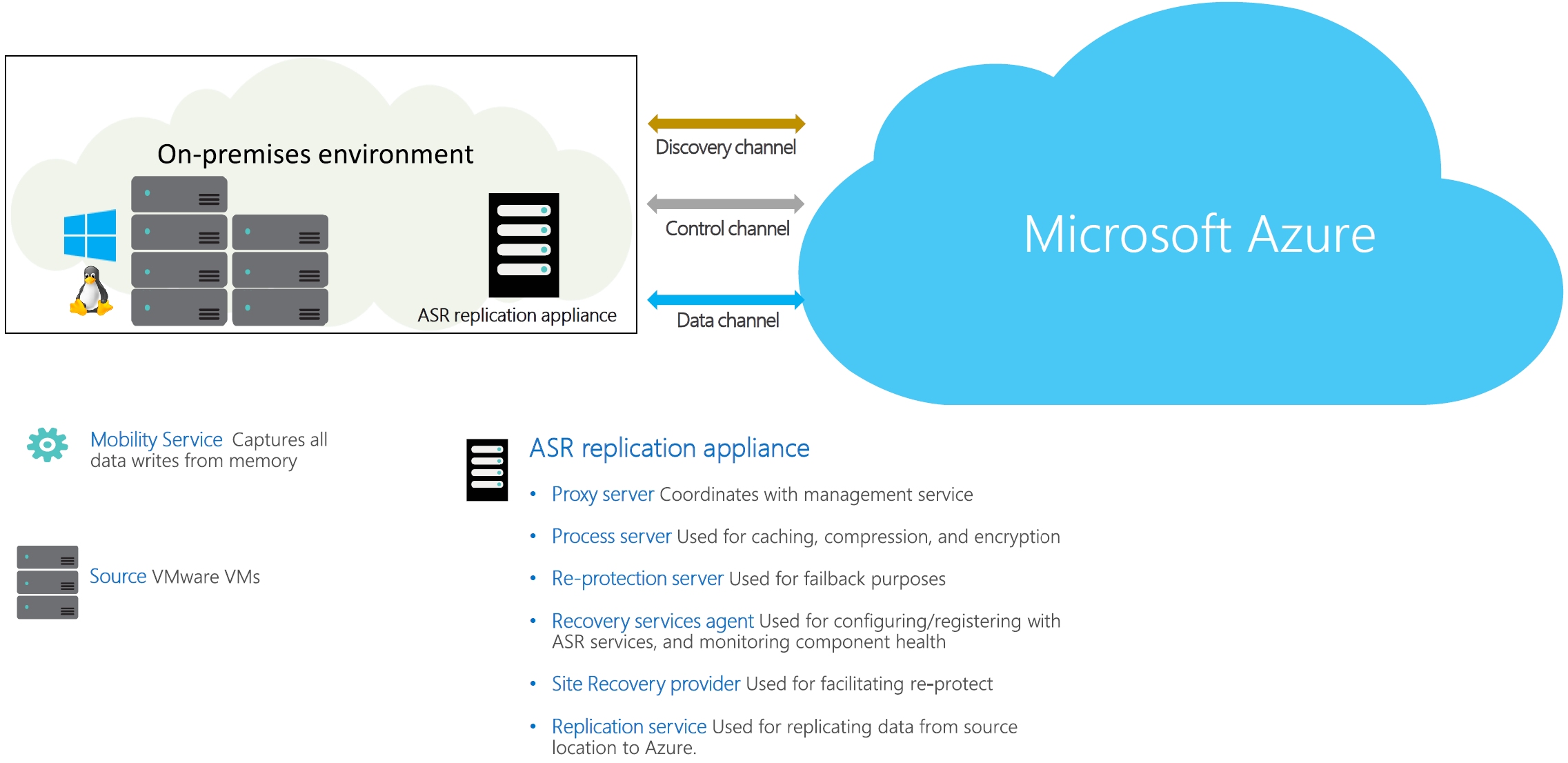
Solved We are using undo/rede logging to secure a system.
4.9 (790) · $ 8.00 · In stock

How i can resolve this? : r/Hacking_Tutorials

Smart Metering Security: How to Protect Your Data and Devices

Mikrotik Security - Securing Your Network with Basic Steps
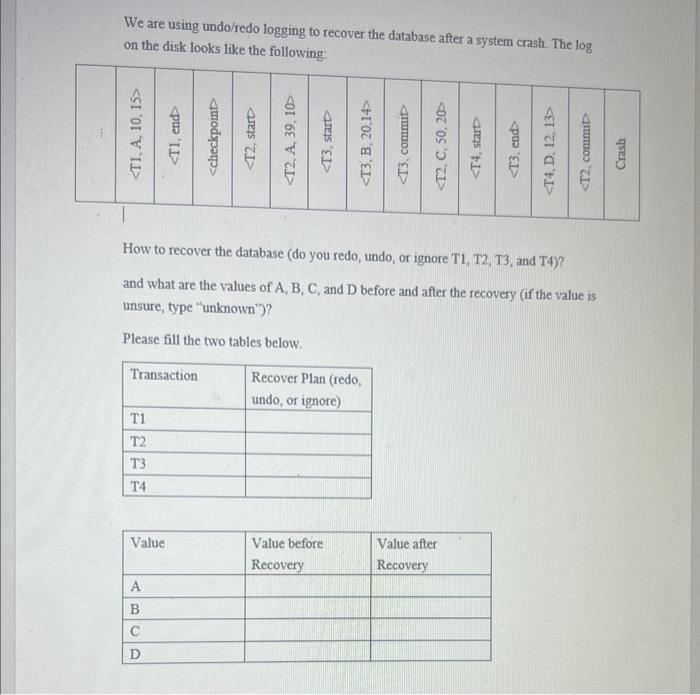
Solved We are using undo/redo logging to recover the

Secure Wireless Access Points

Sobre - Check Point Software

LaaS - Cloud-based Log Aggregation Service

Network Security - Cisco

How to secure your home Wi-Fi network and router
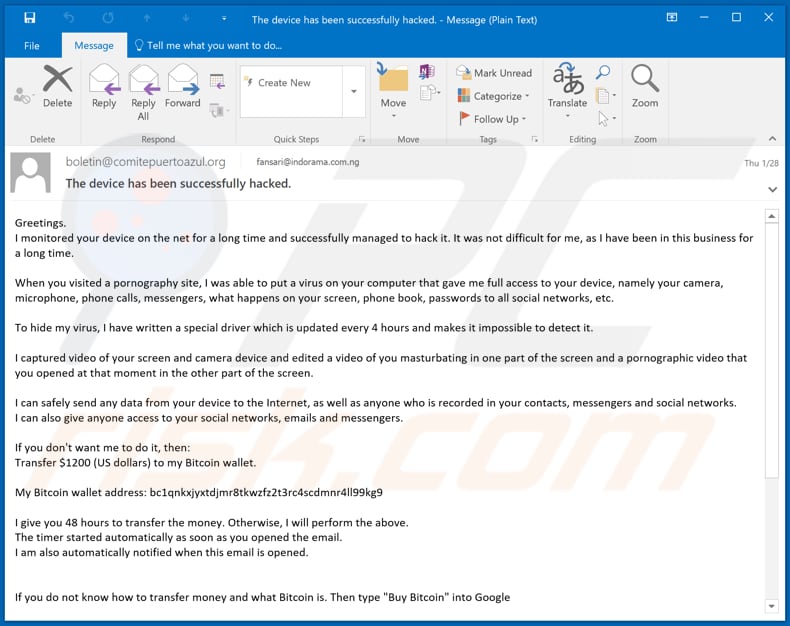
I Monitored Your Device On The Net For A Long Time Email Scam - Removal and recovery steps (updated)
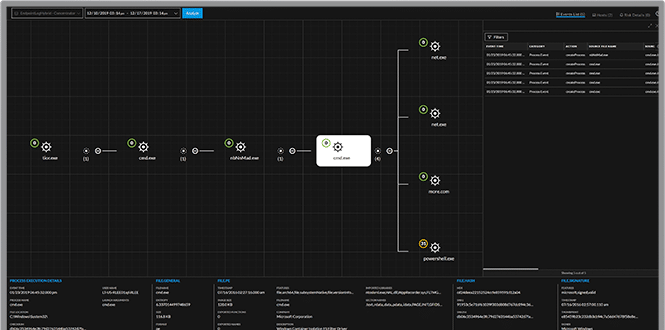
Evolved SIEM – Security Information and Event Management – NetWitness
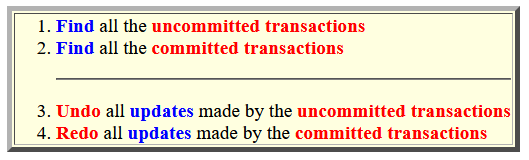
Recovering from a system crash using undo/redo-log
You may also like






Related products
© 2018-2024, bellvei.cat, Inc. or its affiliates