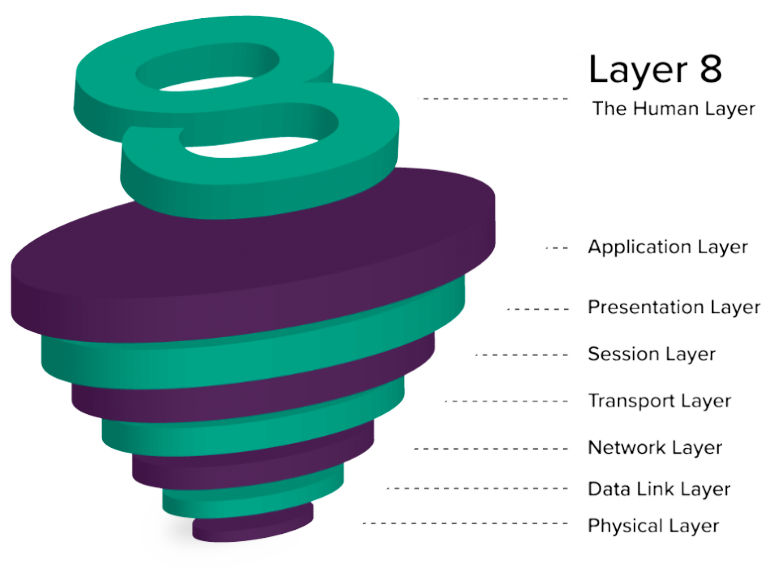
Layer 8 Hacking - Linking the OSI Model with the NIST Triangle
4.8 (260) · $ 12.99 · In stock
Layer 8 Hacking can be defined as hacking above and beyond the technical layers; hacking by targeting the user, the business processes, or the organization i

Securing Layer 8 – Open Sourcerers

Cyber security breakdown: The OSI model

Sensors, Free Full-Text
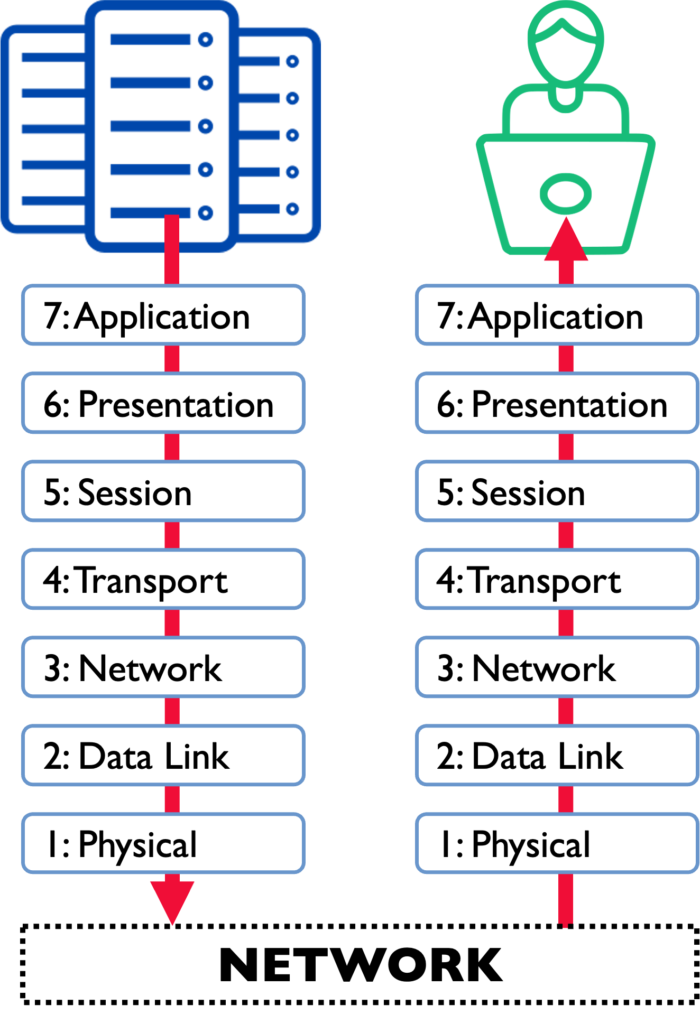
What Is the OSI Model, and How Can We Protect Its Critical Layers

PDF) Modelling computer networks for further security research

Threat analysis for space information network based on network

Security Threats at OSI layers

Introduction To Cyber Security(VIII): The OSI Model.

Security Threats at OSI layers
You may also like






© 2018-2024, bellvei.cat, Inc. or its affiliates